Nextro Insights
-
Closing the Cloud Complexity Gap: The Impact of Fortinet’s 2026 Cloud Security Report on New Zealand businesses
Fortinet’s 2026 Cloud Security Report reveals a growing cloud complexity gap. Learn what this means for New Zealand organisations and how integrated security architectures can improve visibility, resilience, and operational efficiency.
-
Genetec’s State of Physical Security 2026 — What it means for Nextro’s clients in New Zealand & Australia
The latest Genetec “State of Physical Security 2026” report confirms what we at Nextro see every day in New Zealand and Australia: physical & electronic security is no longer just about cameras and locks – it is an enterprise-wide function that’s being redefined by technology, data, and collaboration.
-
Fortinet Cybersecurity Threat Predictions for 2026: Key Lessons for New Zealand Businesses
Fortinet’s 2026 Cybersecurity Threat Predictions Report outlines a rapidly shifting cyber landscape shaped by AI, cloud adoption, identity‑driven attacks, and the growing overlap between IT and OT environments. For New Zealand businesses , critical infrastructure operators, transport networks, and multi‑site enterprises, these trends highlight where security teams must focus over the next 12 months.
-
Genetec Physical Security Trends for 2026: Flexibility, Automation, and Unified Security for New Zealand
Genetec’s outlook for 2026 highlights key shifts in how organisations will deploy and operate physical security systems. These trends carry strong relevance for New Zealand’s airports, councils, critical infrastructure, transport hubs, and multi‑site enterprises seeking to modernise their environments.
-
Strengthening Physical Security: What NZ Boards Need to Know About the PSR Framework
Physical security is now a core component of organisational resilience, protecting people, information, facilities and critical assets. The New Zealand Protective Security Requirements (PSR) provide a comprehensive framework that government agencies must follow, and that private-sector organisations increasingly adopt as a proven best-practice model.
-
Building Geopolitical Resilience in Times of Uncertainty
Discover how New Zealand organisations can build geopolitical resilience amid global uncertainty. Learn how Nextro integrates cyber, physical, and business strategies to help critical sectors anticipate, adapt, and thrive in a shifting risk landscape.
-
Unifying Hybrid Workforce Security with SASE
Fortinet’s 2025 State of Operational Technology and Cybersecurity Report highlights global OT security trends. Nextro shares insights for New Zealand businesses on improving resilience and protecting critical operations.
-
Best Practices for Counter-Drone Deployment at Civilian Airports
New Zealand airports face rising risks from rogue drones. DroneShield’s 2025 white paper outlines best practices for layered detection, non-kinetic mitigation, and operational resilience, insights that Nextro shares with aviation and critical-infrastructure partners.
-
Lessons for New Zealand from the Fortinet 2025 State of OT Cybersecurity Report
Fortinet’s 2025 State of Operational Technology and Cybersecurity Report highlights global OT security trends. Nextro shares insights for New Zealand businesses on improving resilience and protecting critical operations.
-
Learnings from the 2025 Data Security Report
Discover insights from the Fortinet 2025 Data Security Report and how Nextro helps NZ organisations modernise data protection beyond traditional DLP.
-
Why New Zealand IT Managers Must Embrace Operational Technology Security Platforms
As New Zealand’s critical infrastructure and industrial assets become increasingly digitised, cybersecurity risks tied to operational technology (OT) environments continue to rise. In light of these evolving threats, CISOs must rethink their priorities. This Nextro insight explores why embracing an OT security platform is essential for aligning with strategic goals like vendor consolidation and IT/OT convergence.
-
Navigating the 2025 Cyber Threat Landscape
The 2025 Fortinet Global Threat Landscape Report paints a stark picture of an increasingly aggressive and sophisticated cyber threat environment.
-
The Genetec Cloudrunner’s Revolutionary Mapping: Transforming ANPR Investigations Through Geographic Intelligence
Read Nextro’s insight on how Genetec’s precision-based mapping and collaborative camera networks are reshaping vehicle-centric investigations
-
The State of AI in Video Surveillance: Industry Perspectives 2025
In this Nextro analysis, we set out key insights from Axis Communications’ 2025 report on AI in video surveillance. As an Axis Gold Partner and trusted strategic technology partner for many New Zealand businesses, we know that understanding these trends is crucial for our clients seeking to enhance their security posture and gain operational efficiencies.
-
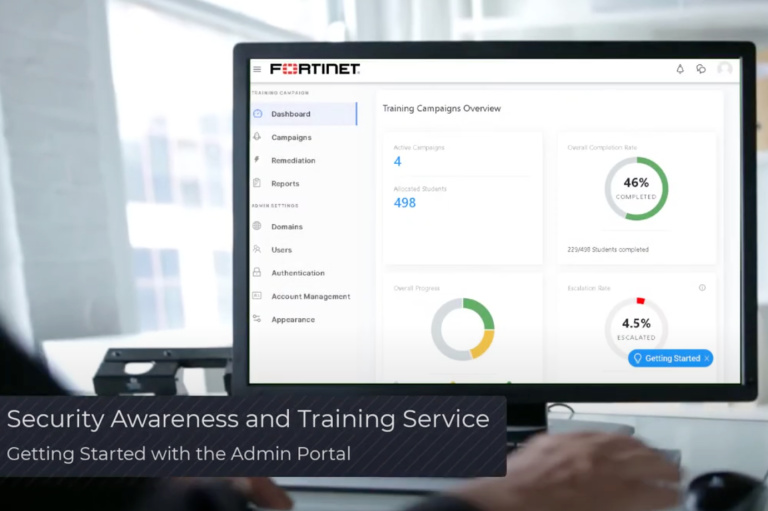
Fortinet’s Global Security Awareness and Training Report: Key Insights for Building Cyber Resilience
Fortinet’s recent Security Awareness and Training Report highlights the growing impact of AI-driven cyber threats. Discover how Nextro’s managed training service helps organisations build a stronger, more resilient workforce and meet evolving security and compliance requirements
-
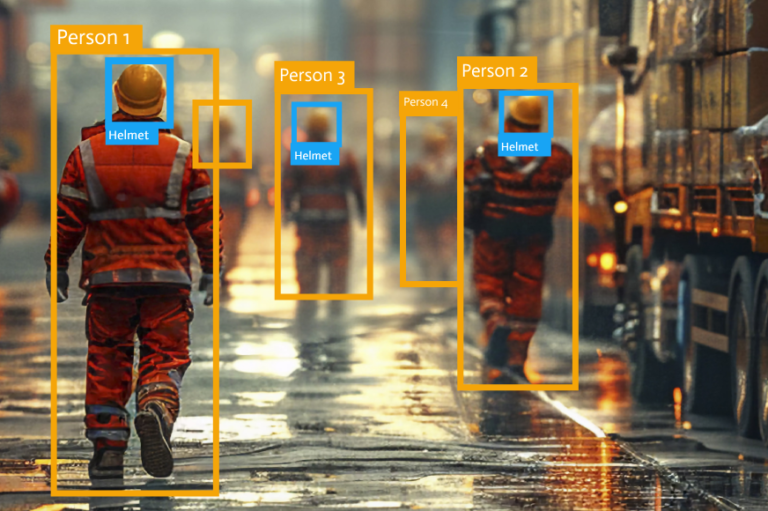
Using AI to Enhance Worker Safety on the Factory Floor
Using AI to Enhance Worker Safety on the Factory Floor In today’s dynamic industrial environments, ensuring worker safety is more important than ever. Traditional safety protocols remain essential, but they don’t always keep pace with the real-time challenges and complexities of modern manufacturing, warehousing, or logistics. Enter Nextro partner Hanwha Vision’s Factory & Safety AI…
-
Why IoT Matters in Physical Security
The Internet of Things (IoT) is transforming the way we connect, monitor, and optimise security infrastructure. With a projected 30 billion IoT devices in use by 2030, organisations are increasingly leveraging these technologies to enhance efficiency, security, and data-driven decision-making. In this article Nextro and Genetec explore how the Industrial Internet of Things (IIoT) is…
-
Enhancing Security with Lockdown: Guidance for Marauding Terrorist Attacks
Lockdown procedures are a critical security measure against Marauding Terrorist Attacks (MTAs). In this article, Nextro explores key insights from the UK’s CPNI on implementing effective lockdowns, highlighting strategies, challenges, and best practices for businesses and security teams in New Zealand and Australia. Stay prepared—learn how to safeguard your site.
-
Navigating the Future of Security: Nextro’s Summary of Top Physical Security Trends for 2025 – from the Genetec Report
Explore Nextro’s breakdown of the top physical security trends for 2025, based on Genetec’s latest report. From cyber-physical security convergence and AI advancements to hybrid-cloud adoption and data-driven decision-making, stay ahead of emerging threats. Learn how these trends are shaping security in New Zealand and how Nextro can help.
-
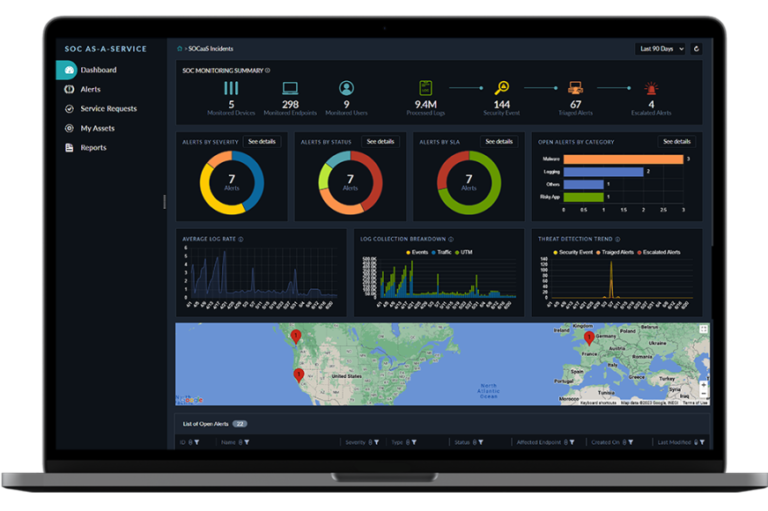
Nextro and Fortinet Partner to Enhance Cybersecurity With 24/7 SOCaaS Monitoring and Incident management
Nextro and Fortinet have partnered to provide affordable 24/7 Security Operations Centre as a Service (SOCaaS) for businesses in Australia and New Zealand. Nextro’s solution, powered by Fortinet, offers continuous network monitoring, advanced threat detection, expert analysis, and regulatory compliance to enhance cybersecurity resilience without the high costs of traditional SOCs.
-
Lessons from the August 2024 Vienna Concert Terror Plot: Security Strategies for Large Events & Critical Infrastructure
Uncover Nextro’s insights on the August 2024 Taylor Swift concert terror plot and its implications for event security and critical infrastructure. Learn key lessons on threat evolution, intelligence sharing, and proactive security measures to protect crowded places, stadia, and high-risk sites from emerging threats.
-
Elevate critical infrastructure networks with Nextro and Arista
Elevate critical infrastructure networks with Nextro and Arista Critical infrastructure industries such as energy, water supply, healthcare, and transportation are the backbone of our society. They are crucial to ensuring public safety, economic stability, and country security. As critical infrastructure managers continually embrace digital transformation, their corporate (IT) and operational (OT) networks must be able…
-
OT environments are facing increasing cyber attacks
OT environments are facing increasing cyber attacks According to a recent global survey released by Fortinet, 31% of organisations with OT environments reported over six intrusions in the past year, a significant increase from the 11% reported the previous year. This alarming finding shows that despite growing efforts and investments to bolster their security posture,…
-
Harnessing AI solutions for security, operational efficiency, and health and safety compliance
Harnessing AI solutions for security, operational efficiency, and health and safety compliance The rise of artificial intelligence (AI) has sparked both excitement over its potential and concerns about its risks. As AI technology continues to evolve, various industries around the globe are exploring its potential applications. AI, which includes machine learning (ML), deep learning (DL),…
-
The Race to Cloudify the LAN
The Race to Cloudify the LAN In 1998, Netflix shipped its first DVD – Beetlejuice – and its online rental service took off like a rocket. But it was the shift that occurred nine years later when they delivered instantaneous access to movies directly to their subscribers’ living rooms, that transformed the industry. Enterprises experienced…
-
Embracing AI: Beyond Tech to Strategic Business Transformation
Embracing AI: Beyond Tech to Strategic Business Transformation AI is a hot topic, with C-level executives, board members, and investors enquiring about the company’s AI strategy. When discussing the integration of Artificial Intelligence in the enterprise, it’s crucial to understand it represents more than just a technological upgrade—it signifies a strategic transformation. A key aspect…
-
Genetec Clearance: Simplify video evidence management with export automation
Genetec Clearance: Simplify video evidence management with export automation Most organisations have established protocols for managing video footage related to incidents that affect their operations, regardless of whether they are security or non-security-related. Efficient video-evidence management protocols help organisations enhance their operational efficiency, reduce the risk of errors, and improve the overall safety of their…
-
Detect, track and engage with an intruder in a restricted area
Detect, track and engage with an intruder in a restricted area In security, staying ahead of potential threats requires technology that offers both reliability and versatility. Axis Communications has once again raised the bar with the release of the new AXIS D2210-VE radar, a sophisticated solution designed to detect, classify, and track intruders in even…
-
Nextro wins NZ Fastest Growing Partner & Transportation Sector categories at Axis Oceania Partner Awards 2024
Nextro wins NZ Fastest Growing Partner & Transportation Sector categories at Axis Oceania Partner Awards 2024 Axis Gold Partner, Nextro, takes out two awards at the annual Oceania Axis partner summit in Denarau Island, Fiji. Auckland, New Zealand, 15 May 2024 – Nextro, the New Zealand security integrator and managed network and security services provider,…
-
Protecting Your Organisation: Introduction to Operational Technology Cybersecurity
Protecting Your Organisation: Introduction to Operational Technology Cybersecurity In recent years, the acceleration of digital transformation has promoted the convergence of corporate/information technology (IT) and operational technology (OT) networks and opened up a realm of opportunities for organisations. IT/Corporate networks encompass an organisation’s computing, networking, and information management aspects, whereas OT networks support devices that…
-
Protect Your Business With Next-Gen Endpoint Security
Protect Your Business With Next-Gen Endpoint Security Next-Gen Endpoint Protection for SMBs Cyber threats are evolving faster than ever before, and small and medium-sized businesses (SMBs) face a tough challenge today. With fewer resources compared to big companies, they become prime targets for cyberattacks. As threats get smarter, SMBs need top-notch endpoint protection more than…
-
Unveiling Hidden IT Costs for SMBs
Unveiling Hidden IT Costs for SMBs Information Technology (IT) has become the backbone for most small to medium-sized businesses (SMBs) in today’s digital age. Managing IT in-house is certainly appealing since you get to control everything, but there’s a catch — the obscured financial drains it introduces often go unnoticed. For SMBs trying to stay…
-
All You Need To Know About Access Points
All You Need To Know About Access Points Access points are crucial in providing wireless network connectivity, allowing devices to bridge wireless connections to a wired network. This comprehensive guide will delve into access points, exploring their purpose, configurations, and the benefits of upgrading. We will also compare access points with wireless routers and Wi-Fi®…
-
Nextro helps Port Taranaki transform its security and operations with new, state-of-the-art, communications room
Nextro helps Port Taranaki transform its security and operations with new, state-of-the-art, communications room Nextro is proud to announce the successful go-live of the unified operations and security centre for our customer, Port Taranaki. This upgrade positions the port at the forefront of modern in-port maritime security and operational efficiency and is the result…
-
Nextro awarded Genetec Partner of the Year for New Zealand at Elevate 24
Nextro awarded Genetec Partner of the Year for New Zealand at Elevate 24 Genetec Unified Elite Partner, Nextro, takes top NZ award in Chiang Mai, Thailand at the Genetec Elevate 24 partner event for the Asia Pacific & Oceania regions. Auckland, New Zealand, 18 March 2024 – Nextro, the New Zealand security integrator and managed…
-
Security Beyond Boundaries: Nextro’s Summary of Top Physical Security Trends for 2024 – from the Genetec Report
Security Beyond Boundaries: Nextro’s Summary of Top Physical Security Trends for 2024 – from the Genetec Report Despite the lingering impact of pandemic-related disruptions, New Zealand businesses are pushing forward, reinforcing their risk management plans amidst labour shortages, supply chain complexities, and escalating physical and cybersecurity threats. At Nextro, we recognise physical security’s pivotal role…
-
5 Ways to Overcome Multifactor Authentication Vulnerabilities
5 Ways to Overcome Multifactor Authentication Vulnerabilities As the digital landscape expands, so do the challenges of securing sensitive information. Multifactor authentication (MFA) has become a linchpin in the defence against cyber threats, yet vulnerabilities persist. In this article, we explore five strategic approaches tailored for IT decision-makers to overcome MFA vulnerabilities, providing a roadmap…
-
Enterprise Networks for the Modern Workplace: A Blueprint for Connectivity and Security
Enterprise Networks for the Modern Workplace: A Blueprint for Connectivity and Security The modern workplace is undergoing a significant transformation. With remote and hybrid work models now the norm, enterprise networks face new challenges in delivering secure, seamless connectivity across distributed environments. Employees now work from corporate offices, home offices, shared workspaces, and on-the-go. They…
-
Wi-Fi, Cellular, or Ethernet? Why Campus Networks Need All Three
Wi-Fi, Cellular, or Ethernet? Why Campus Networks Need All Three Enterprise IT departments face persistent challenges in managing the variety of access network types needed to support today’s users and devices. From stationary desktops to smartphones and tablets, the connectivity needs across a modern campus can vary greatly. Understanding the strengths and limitations of the…
-
Leading the Charge: RUCKUS’s Wi-Fi 7 Platform Sets New Interoperability Standards
Leading the Charge: RUCKUS’s Wi-Fi 7 Platform Sets New Interoperability Standards The Wi-Fi Alliance has selected the RUCKUS R770 access point, part of the RUCKUS Wi-Fi 7 platform, for its Wi-Fi CERTIFIED 7™ interoperability certification test bed. As the only commercial access point in the test bed, the R770 will ensure unmatched interoperability and advanced…
-
Nextro awarded Hanwha Vision Step Partner Gold Status for 2024.
Nextro awarded Hanwha Vision Step Partner Gold Status for 2024. Nextro is thrilled to achieve Gold Partner status with Hanwha Vision. This award recognises Nextro’s early successes with Hanwha’s AI cameras in the New Zealand market. Nextro has deployed Hanwha Vision’s edge-based AI cameras for its customers to surface (in real-time) operational, security, WHS, and…
-
Defending the Digital Fortress: Nextro’s Top Cybersecurity Trends for 2024
Defending the Digital Fortress: Nextro’s Top Cybersecurity Trends for 2024 According to Forbes specialists, cybercrime will cost the global economy more than $10.5 trillion by the end of 2024. This alarming prediction emphasises the increasing need for cybersecurity to be seen as a strategic priority at individual, organisational and governmental levels. In the dynamic terrain…
-
Understanding Financial Risks of Cybersecurity Complacency
Understanding Financial Risks of Cybersecurity Complacency A lack of proper data sanitisation and appropriate methods to manage the entire information lifecycle means those same organisations are providing bad actors with the opportunity to manufacture identity. This situation of storing as much data as possible is creating an Everest-like attack surface, riddled with vulnerabilities and entry…
-
Wi-Fi 7: What Should You Know?
Wi-Fi 7: What Should You Know? As Wi-Fi 7 gains more traction as the latest wireless advancement that continues to make waves in the technology world, RUCKUS Networks has been working on bringing the aspects of this new technology to our readers to help prepare the way for the eventual flood of new devices that…
-
The critical role of Security Awareness: Training in protecting your corporate network
The critical role of Security Awareness: Training in protecting your corporate network In an era of relentless cybersecurity threats, safeguarding your corporate network is no longer an option; it’s an imperative. Malware, phishing, brute force attacks, and other malicious activities pose substantial risks to your organisation’s data and reputation. Investing in Security Awareness Training, your…
-
Protect Your Organisation’s Data with a Zero Trust Network
Protect Your Organisation’s Data with a Zero Trust Network Understanding Zero Trust Able to get past even the most sophisticated and complicated cybersecurity programs, cybercriminals aka “cyberpirates” are stealing vital information from companies right and left. Not to fear – there is a new cyber security approach that is able to stop these cybercriminals dead…
-
The Vital Role of Cybersecurity in Manufacturing Processes
The Vital Role of Cybersecurity in Manufacturing Processes In an era driven by technological advancements, manufacturers are engaged in a constant race against time and competition. Yet, amid the whirlwind of innovation, there’s an unseen menace lurking beneath cyberattacks. Join us as we navigate through the significance of cybersecurity, not just for safeguarding data but…
-
Seamless Network Management
Seamless Network Management RUCKUS One is an AI-driven network assurance and business intelligence platform that enables you to easily manage a converged multi-access public and private enterprise network, make better business decisions, and deliver exceptional user experiences. With flexible subscription and flexible deployment models, RUCKUS One enables you to deploy future-proof networks simply, reliably, securely…
-
Elevating Critical Infrastructure Security with Advanced Surveillance Solutions
Elevating Critical Infrastructure Security with Advanced Surveillance Solutions Critical infrastructure plays a vital role in sustaining nations and their economies. These lifelines, including airports, seaports, railway stations, oil refineries, power plants, and water and wastewater systems, require robust security measures to ensure uninterrupted operation and public safety. Securing the perimeter and ensuring the safety of…