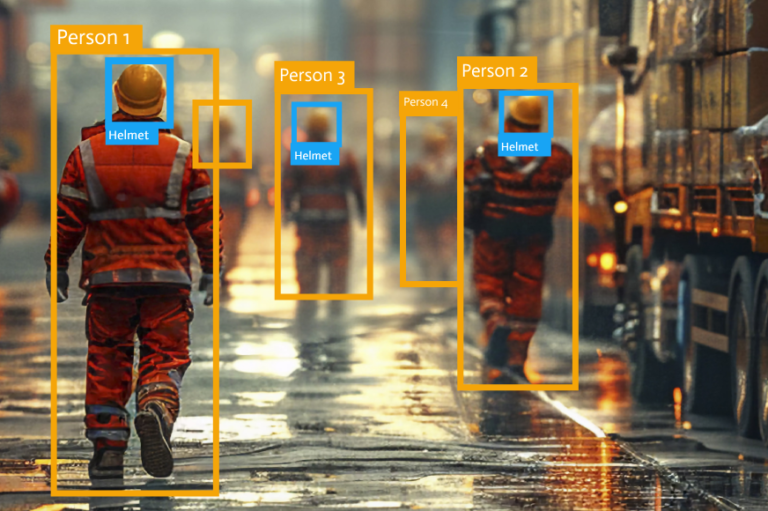
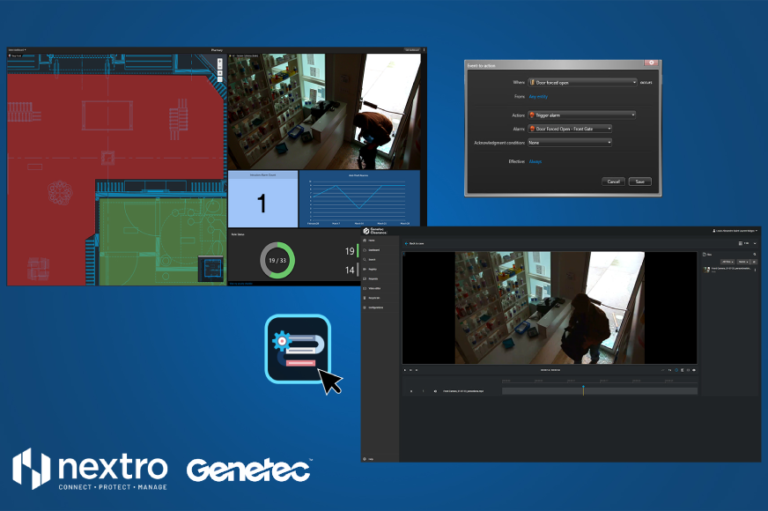
Harnessing AI solutions for security, operational efficiency, and health and safety compliance
Harnessing AI solutions for security, operational efficiency, and health and safety compliance The rise of artificial intelligence (AI) has sparked both excitement over its potential and concerns about its risks. As AI technology continues to evolve, various industries around the globe are exploring its potential applications. AI, which includes machine learning (ML), deep learning (DL),…