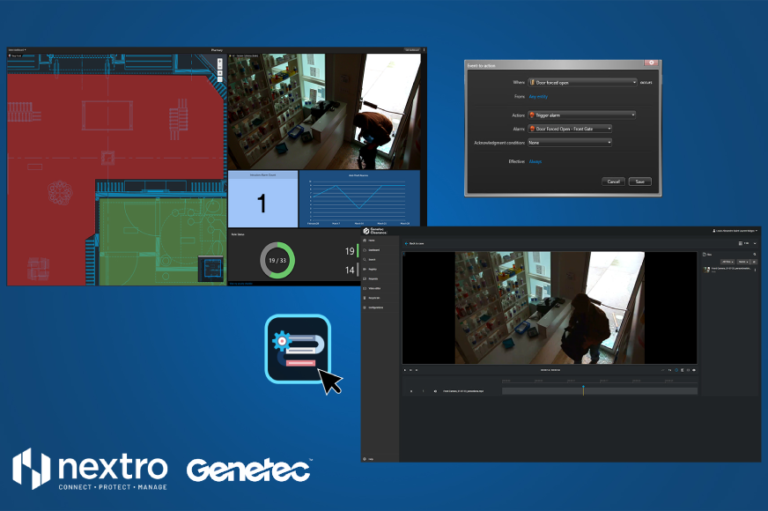
Genetec Clearance: Simplify video evidence management with export automation
Genetec Clearance: Simplify video evidence management with export automation Most organisations have established protocols for managing video footage related to incidents that affect their operations, regardless of whether they are security or non-security-related. Efficient video-evidence management protocols help organisations enhance their operational efficiency, reduce the risk of errors, and improve the overall safety of their…